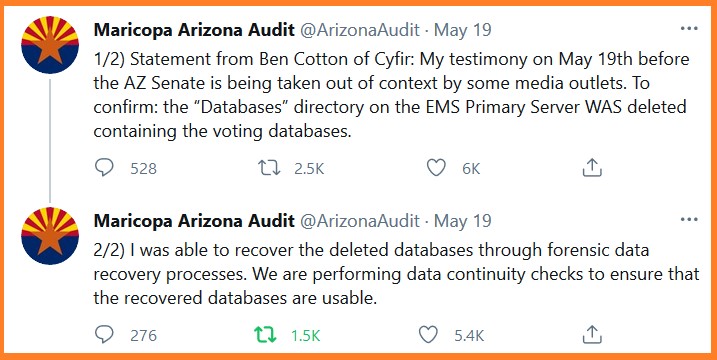
Maricopa County Forensic Auditor: Media & County Officials Intentionally Misleading Public About Deleted Databases
QUESTION – ““Did you determine that the D drive was deleted?”
BEN COTTON – “I did. We follow a very strict forensics acquisition process in which we don’t turn on a system if its delivered powered off. We remove the hard drives and perform forensics imaging with write locks on to prevent any changes to those hard drives. We produce a bit for bit forensics copy of that drive. In the case of the EMS servers, there were 6 drives. 2 drives were for the operating system and they were (unintelligible) configuration. So if something was changed on the operating system drive that would automatically be reflected on both drives.”
“The other four drives were data drives and they were in a RAID configuration known as 1 plus zero. So you have a volume that is mirrored but also data redundancy and striped across both drives. If I don’t turn on a system I don’t have access to the RAID parameters and the county did not provide those to us. so I had to do a discovery process to determine what that RAID configuration was. Part of that process is a scan across those drives to detect partitions of data and to also detect a master file table which is a record of all of the directories of the files that are contained in that partition, and a pointer to where that data resides on the hard drive. In the course of performing that discovery I found that an MFT that clearly indicated that the data base directory was deleted from that server. All of this may be moot because subsequently I have been able to recover all the deleted files and I have access to that data.”




Post a Comment